Behavioral Information Security Part 1: The Failure of Contemporary InfoSec
· @jabenninghoffThe different areas of knowledge and expertise within Information Security can fairly be described in four categories: Physical, Technical, Policy, and People.
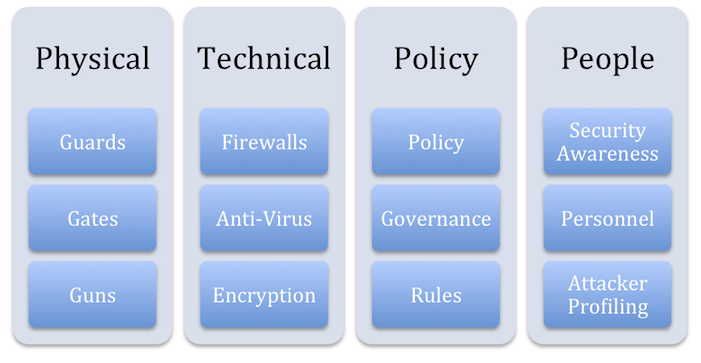
Physical security is very well understood, as it has been part of human knowledge for as long as there have been people, we’re generally good at it, and it hasn’t fundamentally changed since the days when computer security was the guards, gates, and guns.
The story is similar for Technical security – firewalls, anti-virus, access controls, tokens, etc., has been around since the advent of timesharing systems created the need for the password. We’re not as good at technical security as physical security, but we’re pretty good. There’s always room for improvement, of course, but this is clearly an area of strength for the profession – just look at the skills listed for a typical security job posting: Firewall, IDS/IPS, Network, Administration, Active Directory, Anti-Virus, etc.
On Policy, which includes written policy, governance, program organization, etc., we are weaker; most companies now have a security policy, although not all do, and as we know, the policies aren’t always well written or well implemented. Still, we do have established policy frameworks, like the ISO 27000 series and other tools to address problems of policy and governance.
For the final category, people, we’ve largely failed as a profession. Historically, we’ve tried to force people to adapt to the technology we built, and then blame the user when they fail to use it properly – the talking point is, “people are stupid, and you can’t fix stupid.” Security Awareness training, one of the few tools we have to address people problems, has been and continues to be poorly executed. At best, Awareness explains security rules well enough so that we can fire people when they break them, and at worst is a series of posters asking people to “do good things,” with no evidence that it is even effective. Although we have started to improve, our understanding of human/computer interaction is poor, and we do little, if any, to understand the motivation and behavior of both external attackers as well as internal personnel.
The failure of InfoSec to address people is understandable, considering the origins of our profession. Before Information Security, there was computer security – the interaction of people, computers, and information. The IT professionals became IT Security professionals, a path that is still typical for many Information Security professionals today. However, by changing from IT Security to Information Security, we expanded our purview to the interaction of people and information, moving beyond the world of Physical and Technical controls.
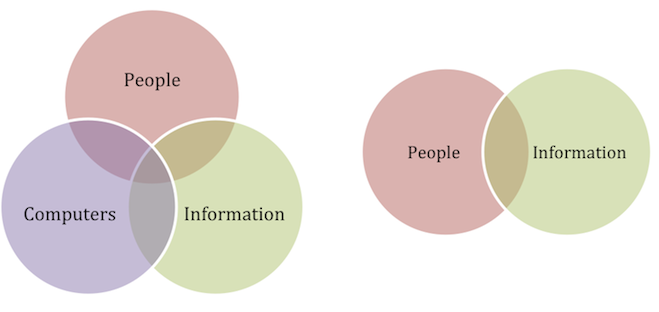
Being computer professionals first, our focus remained on what was important in computer security, the information and the technology protecting it. The failures of security to address issues in the people realm are largely due to the information-centric model. A new, people centric model is needed to develop the tools we need.
In the next article, I’ll introduce the Behavioral Information Security model, which places people at the center, a philosophical shift in thinking that can help us tackle the “people problem.”